EBooks
Browse our eBooks
Building an Effective Backup and Disaster Recovery Plan
To protect your organization’s data, records, and intelligence, you need to have backups in place and an effective disaster recovery plan.
Stay Focused on Your Business with Managed IT Services
When your tech malfunctions, that’s just one more thing on your already overcrowded plate.
CONVERGING BUSINESS KNOWLEDGE WITH IT SKILLS
It’s a difficult balance, however, and it can be all too easy to lose focus of your business goals in favor of managing IT.
RISK ASSESSMENT
DON'T WAIT FOR DISASTER TO STRIKE
Request your assessment today! CyberTeam’s risk assessments are designed to help you address threats to your business so you can protect your data, your bottom line, and your people.
UNRAVELING THE POWERS OF AN IT CONSULTANT
IT consultant services can streamline workflows, improve response times to customer inquiries, and maximize efficiency.
16 Questions You Need to Ask
When Evaluating a New IT Provider
Discover the essential questions that will help you compare IT providers.
All Services: Explained
Managed IT Services is a big term with a lot of moving parts. To help you understand the value CyberTeam provides to our clients, we wanted to provide a breakdown of the expertise we provide in our service in non-technical terms.
Guide to Auditing Technology Bills
You know your IT bills are coming, but it's often hard to make any sense of them. In this guide, we'll break down your typical technology expenses and how to audit them: you’ll be able to understand each section and prepare pointed questions to identify if you're getting back value for your payments.
Guide to Transitioning
to a New Managed Service Provider
Many business owners believe this process is difficult, but as long as you choose the right provider, there should be no downtime for the end users and yourself. Don’t settle for a subpar provider because you’re afraid of a transition. As long as you did your due diligence in the hiring stage, you’ll be in good hands.
Top 7 Reasons
You May Be Considering Leaving Your IT Provider
We’ve compiled this list based on the complaints we hear from prospective clients.
Insider Threat Protection
An insider threat is an individual employed by the company that uses their access for nefarious activities.

Email Threats
Email is a key way that hackers gain access to organizational data.
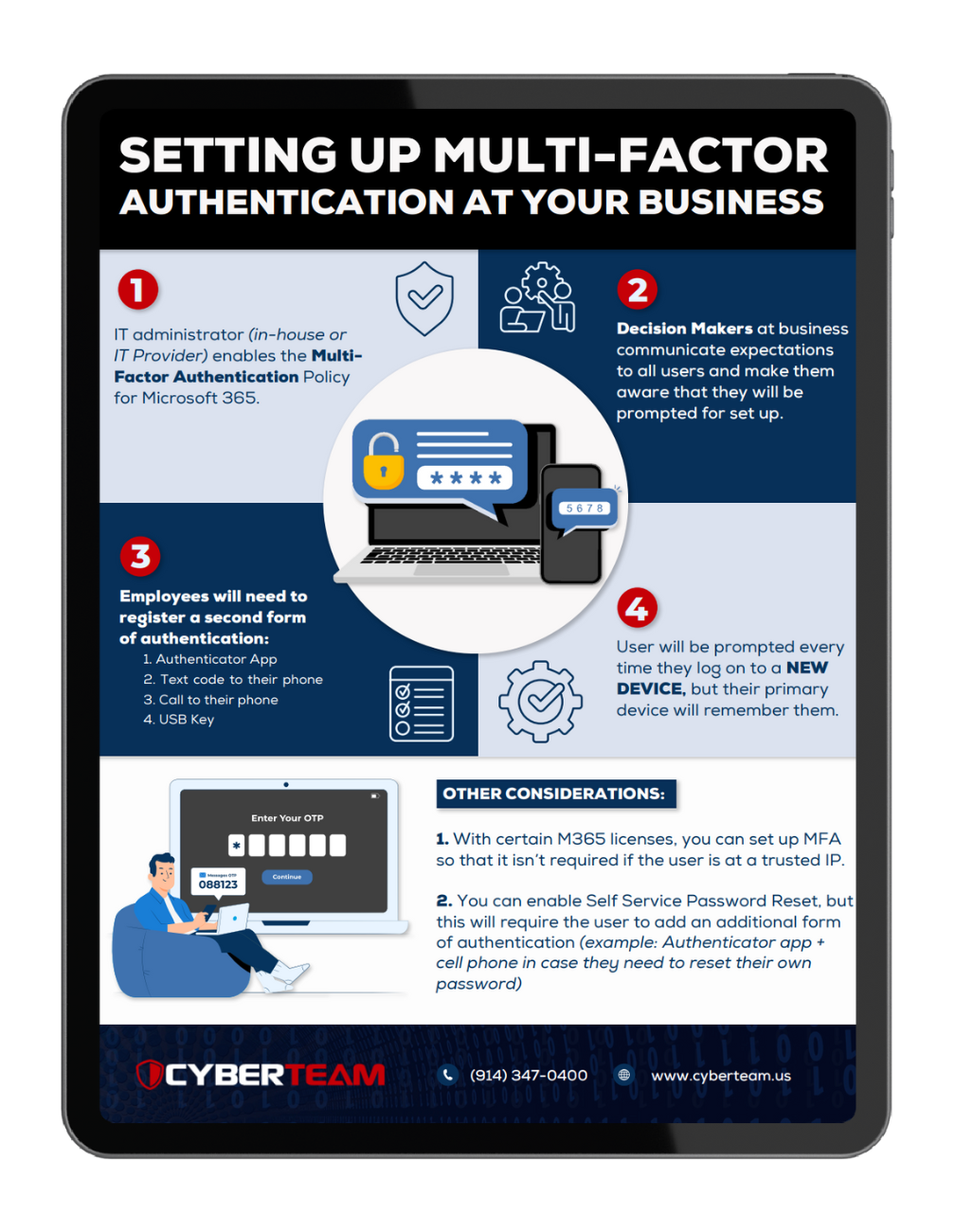
Setting Up Multi-Factor Authentication
Strengthen your cybersecurity by setting up multi-factor authentication (MFA) at your business.











